Cauliflower Hash Browns | Recipe | Cauliflower, Easy cauliflower recipes, Cauliflower hash brown recipe

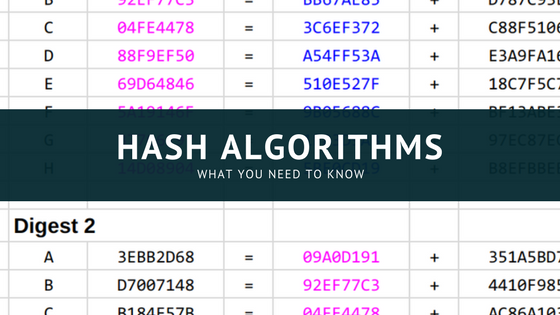
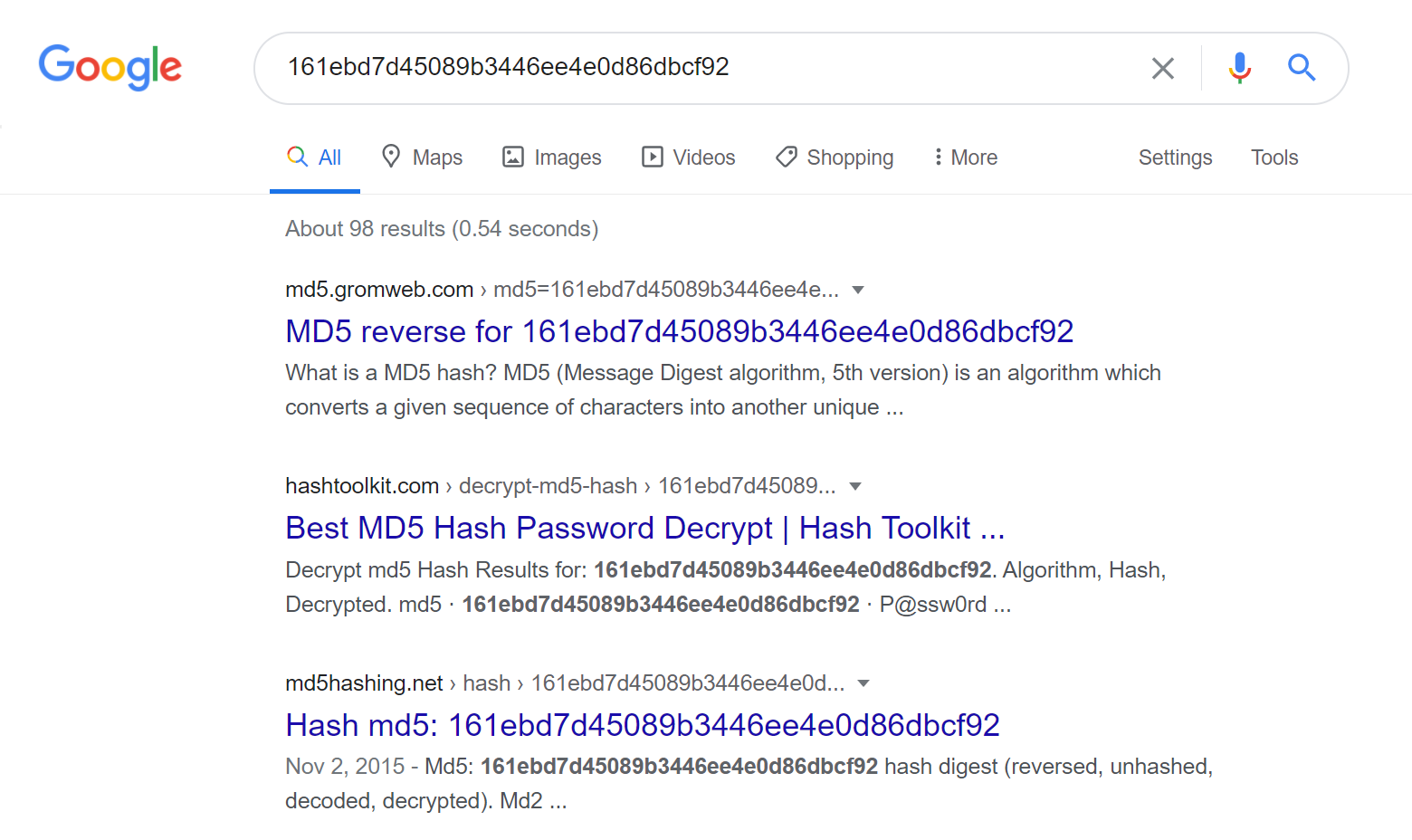
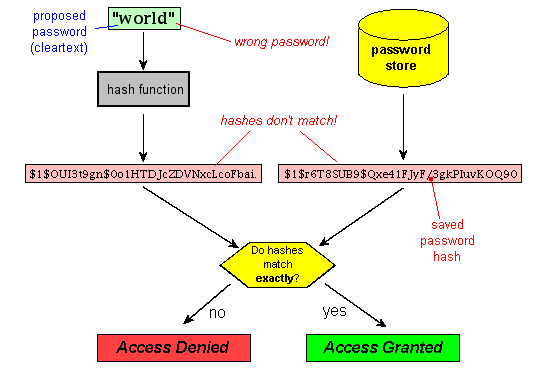
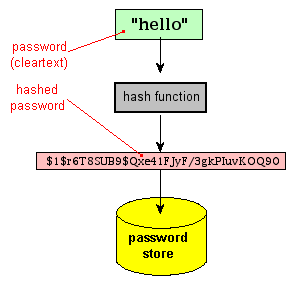
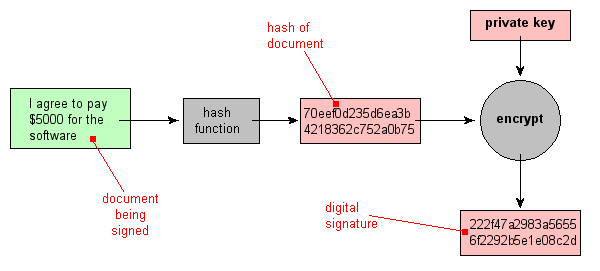
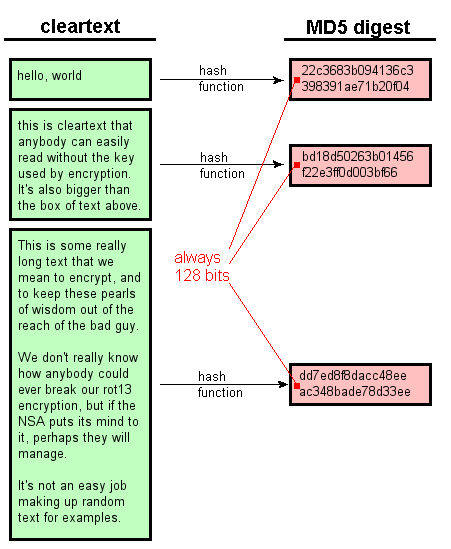
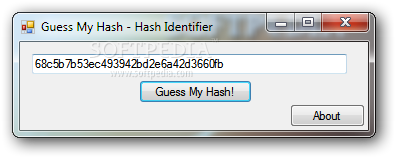
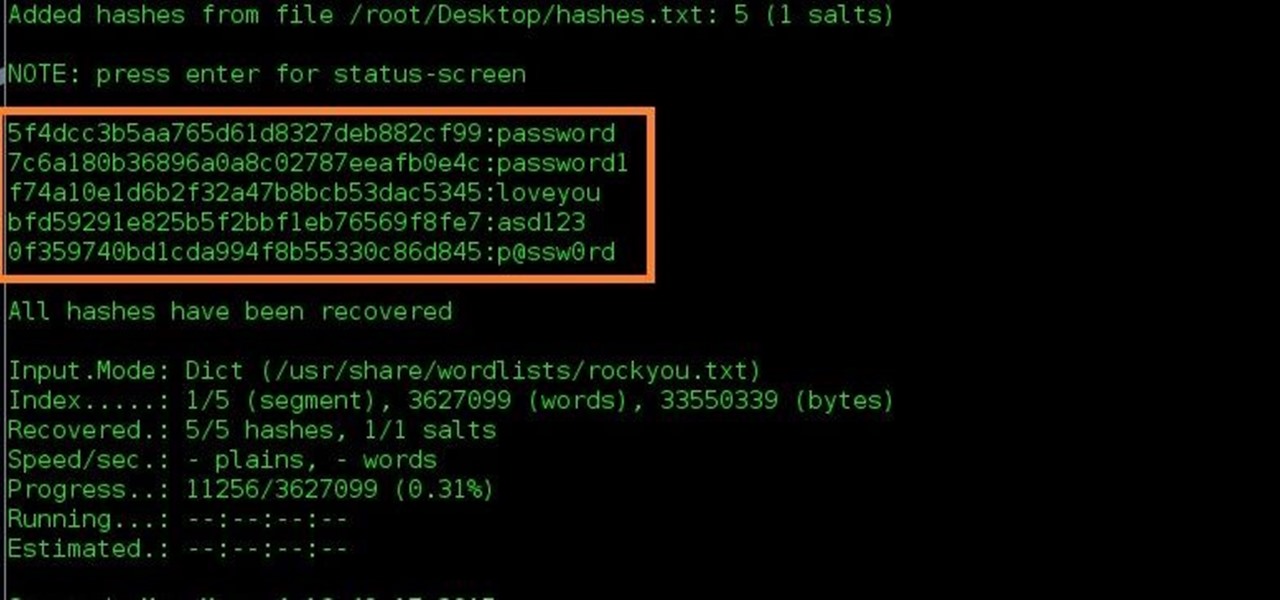
Password Hashes — How They Work, How They're Hacked, and How to Maximize Security | by Cassandra Corrales | Medium

Password Hashes — How They Work, How They're Hacked, and How to Maximize Security | by Cassandra Corrales | Medium